Privacy for your Smartphone is not won innate!
Convinced by the adage “To live happily, let's live hidden”? Let's see how to put it into practice.
When we talk about the security/confidentiality of our “mobiles”, we're really talking about the operating system that runs them. 75% run on Android (based on Google-sponsored Linux under open-source license), the remaining 25% mainly on iOS (based on Unix under Apple's proprietary license). While it is often preferable to turn to open-source solutions, as this guarantees that the code is audited and that there are no “backdoors”, the following points should be borne in mind when it comes to operating systems:
- Since the majority of mobiles run on Android, this makes this OS (Operating System) more attractive to attackers.
- While open-source makes for a customizable and therefore potentially more secure OS, it also makes it more “open” and therefore less secure when the versions deployed by manufacturers are customized to natively use registered data => ditto for app stores, which are less controlled.
For these reasons, iOS is more secure than Android and less prone to attack. It is also more respectful of privacy (up to a point of course). A study by Douglas C. Schmidt, professor of computer science at Vanderbilt University in the USA, shows, for example, that an idle Android smartphone communicates with Google 10 times more than an iPhone communicates with Apple servers, or that an Android smartphone running Chrome sends 50 times more data collection requests than an iOS smartphone running Safari. Although already more discreet than Android, iOS allows you to go one step further by further restricting the amount of data collected and transmitted.
=> Below are some suggested settings to limit iOS data collection and make it more secure. But be aware that the “wow” factor, the practicality generated by your smartphone's features, is often in direct opposition to the concepts of privacy and security.
iOS security settings:
- Use a “serious” unlock code (not 0000 or 1234) =>
Settings/Face ID and Passcode/Change Passcode/Code options - Set "Require Face ID" for your sensitive apps by touch and hold the app icon.
- Restrict access to functions when screen is locked =>
Settings/Face Id and Passcode/Allow access when locked - Enable “Erase data” after 10 access attempts =>
Settings/Face ID and code/Erase data - Enable automatic iCloud backups (see top line for utility of backups) =>
Settings/iCloud/ICloud Backup - Automatically install security updates (because security holes are where the problems come from) =>
Settings/General/Software Updates/Automatic Updates - Use the included “iCloud Keychain” password manager or a cross-platform one (Bitwarden) =>
Settings/Apps/Passwords/View AutoFill Settings/Autofill Passwords and Passkeys & AutoFill From
iOS privacy settings:
Since iOS 16 (early 2023), Apple finally offers to make virtually all your iCloud data confidential.
- Activate End To End Encryption (E2EE) =>
Settings/iCloud/Advanced Data Protection. This is also essential if you want your iCloud private keys to be stored on your device and not at Apple.
| Main types of data. | STANDARD Protection | ADVANCED Data Protection E2EE |
|---|---|---|
| iCloud Mail | [No] | [No] |
| Contacts | [No] | [No] |
| Calendars | [No] | [No] |
| iCloud Backup | [No] | [Yes] |
| iCloud Drive | [No] | [Yes] |
| Photos | [No] | [Yes] |
| Wallet passes | [No] | [Yes] |
| Passwords and keychain | [Yes] | [Yes] |
| Messages in iCloud | [Yes] | [Yes] |
| Apple Card transactions | [Yes] | [Yes] |
| Health/Home | [Yes] | [Yes] |
- Disable access to iCloud on the Web (otherwise your private keys will be on Apple's servers) =>
Settings/iCloud/Access iCloud data on the Web. - Hide your IP address to browse anonymously =>
Settings/iCloud/Private relayotherwise use a VPN (Proton VPN). - Use “disposable” emails for all website registrations to avoid spam =>
Settings/iCloud/Hide my email address. - Use a secure mail/calendar/contacts provider (Tuta Mail) and not the natively provided Mail/Contacts/Calendars (see table above to understand why).
- Disable automatic listening to Siri (the in-house voice assistant) =>
Settings/Siri/Detect “Dis Siri(But if you deactivate it entirely, you'll no longer have access to the CarPlay feature, which is so handy in the car).
Now go to Settings/Privacy and Security.
- Deactivate the "Location Services" items
“Suggestions & Search”-“Significant locations”-“PRODUCT IMPROVEMENT”in the“System services”. - Disable
“Allow Apps to Request to Track”in“Tracking”. - Disable
“INCLUDE SUGGESTIONS FROM”in“Journaling Suggestions”. - Check data in
“Safety Check”. - Disable all
`Analytics and improvements". - Disable “Personalized Ads” in “Apple Advertising”.
- Take a look at
TRANSPARENCY LOGS “App Privacy Report”to find out more, and find that many apps send data to ... Google!
With all these changes, we've already taken a big step in restricting Apple's intrusion into our digital lives. (Sorry, let me rephrase: in the degradation of the user experience 😊). But if these settings have to do with the general operation of the iPhone, we now have to deal with the behavior of the main apps we use on a daily basis, and which also know a lot about us. If only they would record and transmit data without warning...
To give you an idea of the confidentiality of some of the best-known applications on the market, you'll find below a fine example of the data collected by Gmail compared with Tuta Mail. It's only declarative on the Apple app store, but it gives a small idea of the subject (for more exhaustiveness consult the famous “App Privacy Report” mentioned above).
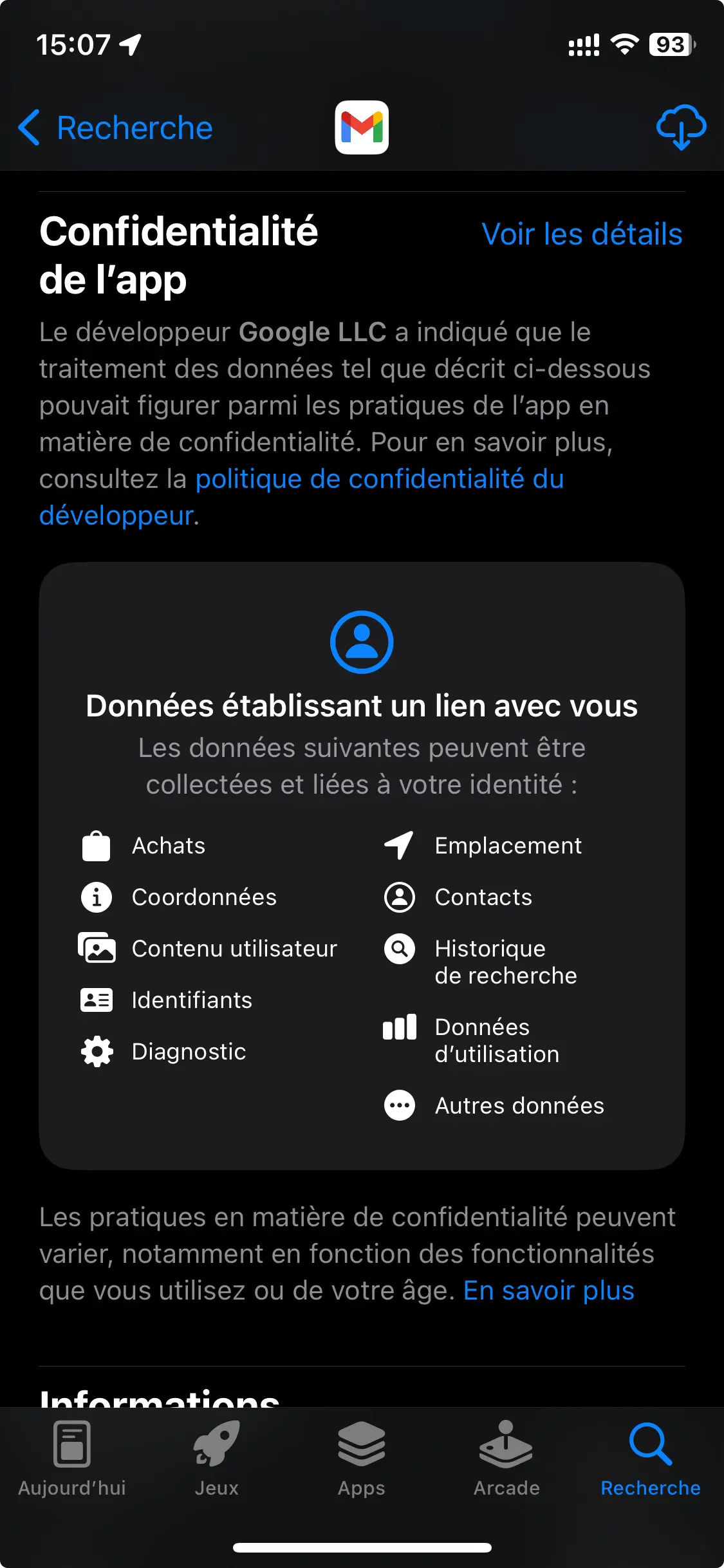
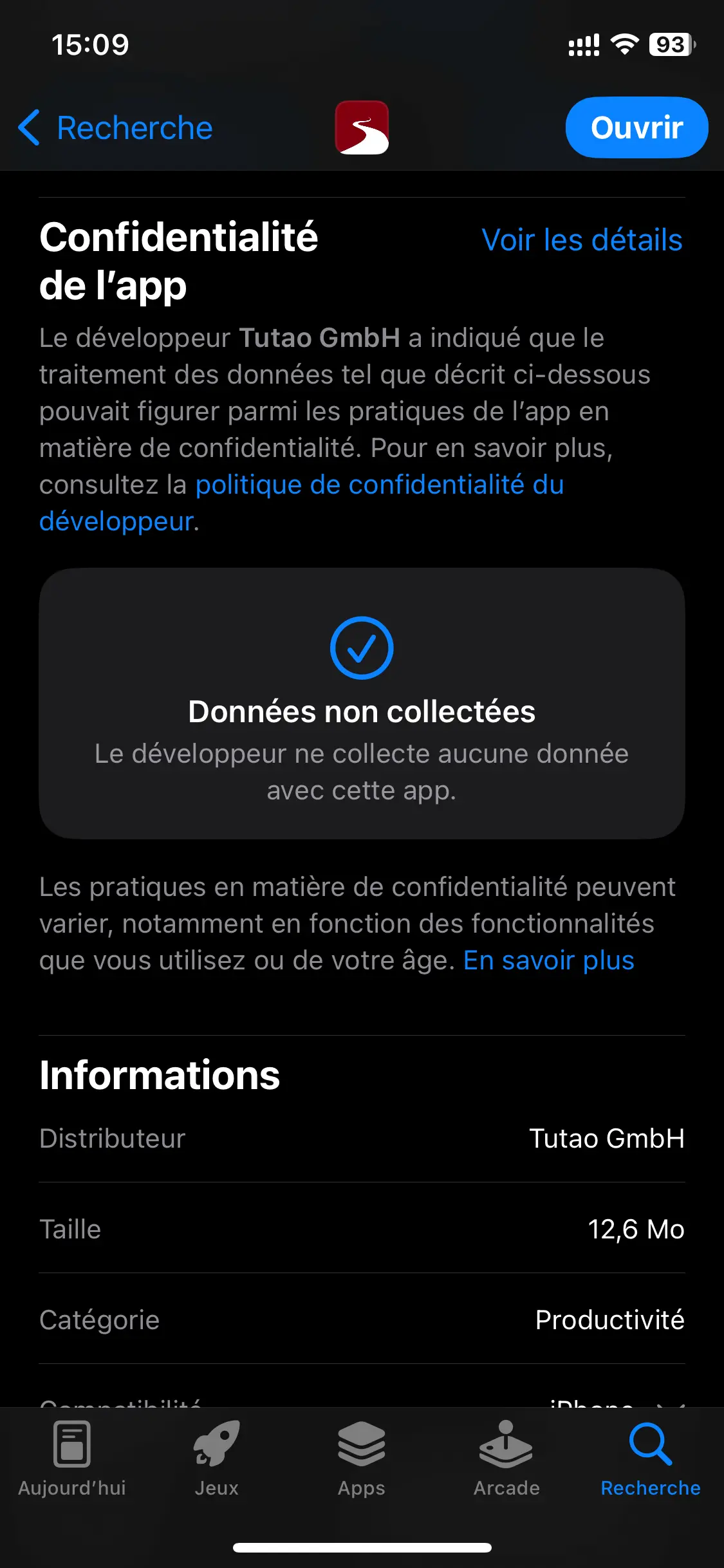
App privacy settings
SAFARI Browser
This browser is historically the one supplied by default with iOS. However, since the DMA (Digital Markets Act) imposed by the European Community, things have changed a little. Apple has been forced to open up its system since March 2024 on versions after iOS 17.3 in order to comply. So you can now set a default browser other than Safari. To do so => Settings/Desired browser app/Default browser app.
Except on iOS startup after a system update, when a dozen browsers are offered, you'll need to have the chosen browser already installed to be able to set it as default. If you want to switch to Tor, DuckDuckGo or Startpage, that's fine, because you'll be taking a big step towards privacy. If you want to switch to another browser, think twice...
Note that Safari is not necessarily the worst choice:
- The “Private Relay” feature that hides your IP address only works with it.
- It's the browser with the fewest security flaws of the major browsers on the market (including Chrome, Firefox and Edge).
There are, however, a number of adjustments you can make to limit potential risks:
- Strictly limit browser extensions, which remain important attack vectors (even if the Apple ecosystem limits them natively).
- Block Pop-ups in =>
Settings/Apps/Safari/General. - Prevent cross-site tracking by disabling it in =>
Settings/Apps/Safari/Privacy & Security. - Hide IP address in =>
Settings/Apps/Safari/Privacy & Securitymenu - Increase the privacy level for advertising measures in =>
Settings/Apps/Safari/Confidentiality & Security. - Using Private Browsing mode does not prevent the servers consulted from storing your connection details. It only means you won't have a local history and won't save cookies.
Generally speaking, disabling “Suggest app” and “Learn from this app” restricts systematic data collection.
Search engine It is set up in 'Settings/Apps/Safari/Search engine' and iOS only natively offers 5 of them:
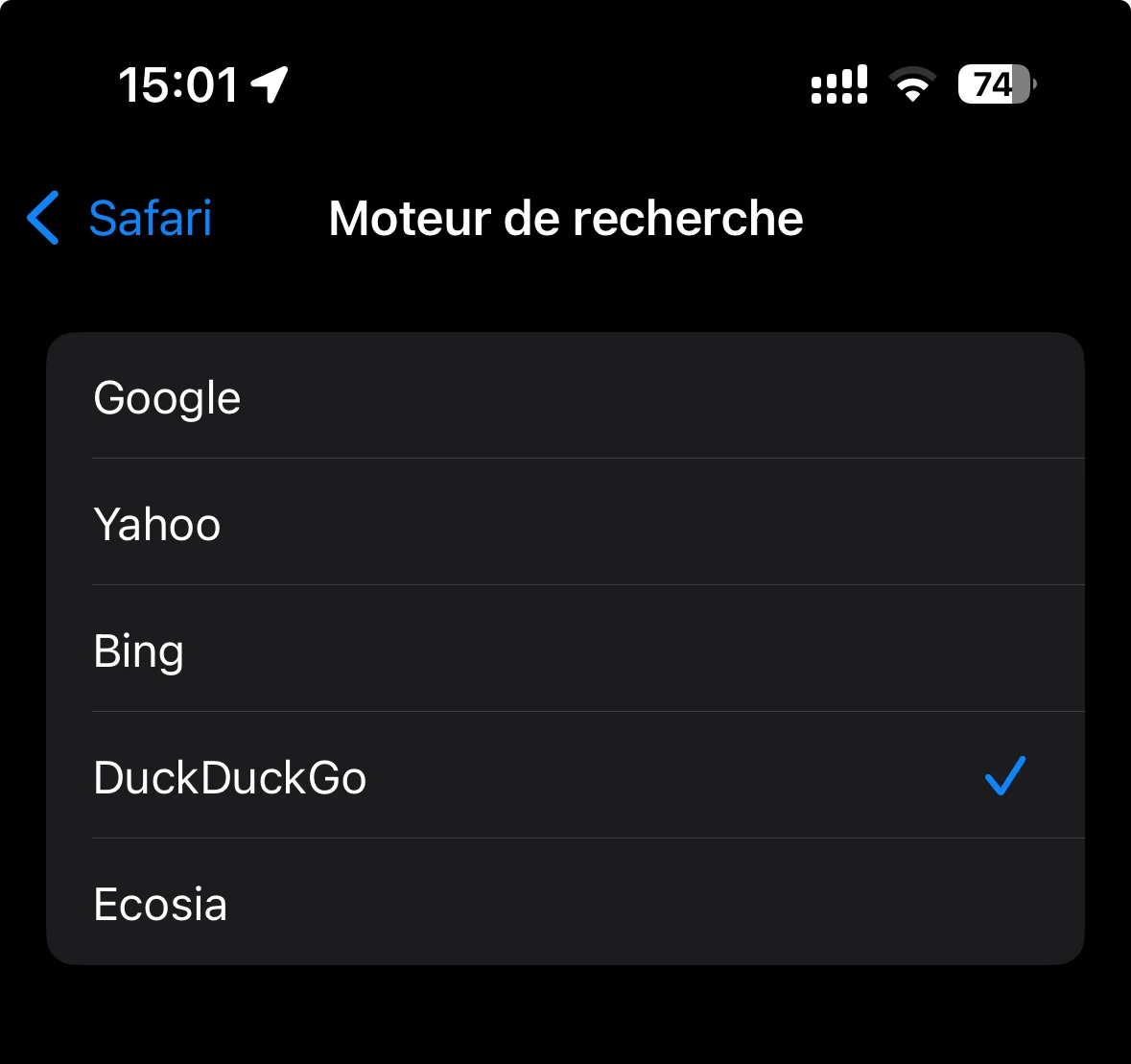
In this field, Google remains for many a benchmark in terms of search efficiency. However, when you consider its indirect price (see data collection above), it's clear that it should be avoided. If you've made this choice, which has unfortunate consequences for your personal data, I'll leave you to find out how to deactivate all the associated trackers... If you'd like to use more respectful trackers that collect neither your IP address nor your personal data:

DuckDuckGo was founded in 2008 by Gabriel Weinberg. This American search engine uses the search results of Bing, does not collect any personally identifiable data or IP addresses.

Startpage was launched on July 7, 2009 and was previously known as Ixquick. This Dutch engine, which uses search results from Google behind a proxy (Anonymous Mode), deletes IP addresses, various tracking cookies and personal data.
Important note: although these engines don't collect data when you search, they can't prevent your data from being collected when you click on the sites in question. To compensate for this weakness, Startpage goes one step further and offers to connect to sites in “Anonymous View”. The connection is established behind a proxy.

MAIL application
As we saw above, E2EE encryption is not available for SMTP/IMAP e-mail applications, nor for the Contacts/Calendars associated with them. You should therefore avoid using MAIL, preferring a third-party application (e.g. Tuta Mail).
If you still resist, there's a setting to hide your IP address and load remote content in the background (to avoid spy pixels) => Settings/Apps/Mail/Privacy Protection.
Spy pixels are trackers that enable advertisers to draw up marketing profiles based on information gathered when you open their e-mail: this lets them know that you've opened it, for how long, from what type of hardware and software platform, etc...
There's also the option of using the DuckDuckGo Email service, which will forward emails received on the address created as “@duck.com” to your regular email after cleaning them of any trackers present in the images or links included. It is also possible to reply to an email received from this @duck.com email address. There's also a “Generate a private Duck address” feature in their application, which, like Apple's “Hide my e-mail address”, lets you create random addresses to be used when filling in forms on the net.
With regard to the general use of e-mail applications, it's worth remembering that it's strictly forbidden to click on a link received by e-mail, as this is the main vector for Phishing attacks. If you need to connect to a site and identify yourself, use the password manager to make sure you land on the genuine site.
Other applications Confidentiality means prohibiting (or at least limiting) the data collected that can be used to link our browsing to our real identity. We've seen that the right privacy settings, coupled with the use of iCloud+ “Private Relay”, can achieve this objective when browsing the Web with Safari (or by using Startpage in Proxy mode). But this is not the case at this stage when using your many applications! For this there is only one way to prevent you from being tracked using your IP adress => use a VPN (Virtual Private Network)..
Virtual Private Network (VPN)
How the Internet works
Basically, for us private individuals, each of our connected terminals is identified by an IP address for Internet Protocol. This IP address is of the type “---.---.---.---”. All connected terminals have an IP address. It's local and private, like 192.168.1.0/254 up to your router (the famous “Box”). The router itself has a public IP address, which may look like xx9.7.105.24 in IPv4 format (4 integers separated by a dot) or “xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx” in IPv6 format. The IPv4 format is destined to disappear, as its format (32 bits) only allows the allocation of 232 or 4,294,967,296 IP addresses. The last address was allocated in Europe in 2019. Since 2017, it has been replaced by 128-bit IPv6 addresses such as “20xx:db8:0:85a3:0:0:ac1f:8001”, which allows 2128 or billions of billions of billions of billions of possibilities (340 sextillons), so we can rest easy...
Connecting to a site means creating a link, a route, between your terminal, identified by its IP, and the site you're visiting. Fortunately, you don't need to know the IP of every site on the Net. A directory of this type does exist, but to use it as it is would take us back to the bygone days of postal directories... This directory, this database, is called DNS for Domain Name Service, and is responsible for translating each domain name into an IP address.
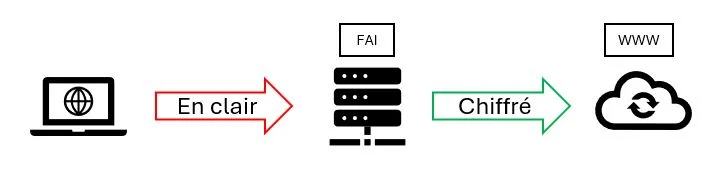
When you visit a website, your request is handled by your ISP (Internet Service Provider), which routes it to the Internet, i.e. to the servers that will connect you to the site you're looking for.
The problem is that traffic between your terminal and the router is not encrypted: encryption only takes place beyond the router, by activating TLS (Transport Layer Security) => so your ISP is able to track all your activity.
How VPN works
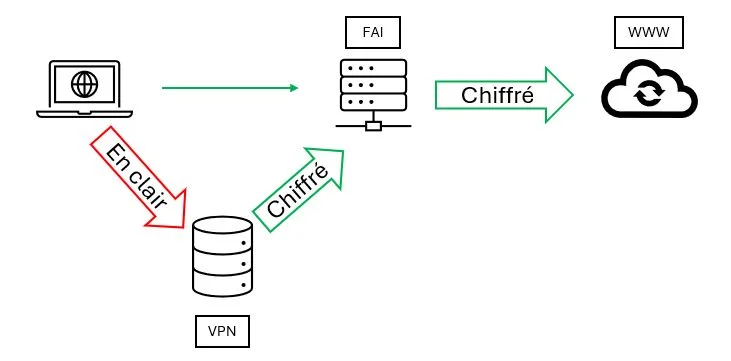
This is where the VPN provider comes in, like Zorro. It places a server between your terminal and the router. This server will retrieve your request, encrypt it and transmit it to the router with a new IP address.
Result:
1- => your ISP only sees encrypted traffic.
2- => the site you are visiting is no longer able to identify you since it is a new IP assigned by the VPN that is now displayed.
If surfing the Web without a firewall exposes us to the curiosity of computer servers in our path, let's not forget that the applications we download and often use instead of our browsers are (for many) guilty of the same indiscretions...
Consequences to be drawn:
- Downloading an application while protected by a VPN is a good idea to avoid any attempt at tracking by your ISP.
- Then, check whether the application's designer has natively provided for automatic transmission of usage data (the Gmail example above) can be very instructive.
- Finally, using this application with a VPN activated will preserve the confidentiality associated with its use.
But by the way, are you aware of the type of data that your IP reveals about you? Discover below some of the elements that an IP data provider is able to provide from this identifier. And everything goes...
{
"ip": "185.195.71.215",
"hostname": "185.195.71.215",
"continent_code": "EU",
"continent_name": "Europe",
"country_code2": "CH",
"country_code3": "CHE",
"country_name": "Switzerland",
"country_name_official": "Swiss Confederation",
"country_capital": "Bern",
"state_prov": "Zurich",
"state_code": "CH-ZH",
"district": "Zurich",
"city": "Zurich",
"zipcode": "8001",
"latitude": "47.37700",
"longitude": "8.53977",
"is_eu": false,
"calling_code": "+41",
"country_tld": ".ch",
"languages": "de-CH,fr-CH,it-CH,rm",
"country_flag": "https://ipgeolocation.io/static/flags/ch_64.png",
"geoname_id": "6530239",
"isp": "Datasource AG",
"connection_type": "",
"organization": "Datasource AG",
"country_emoji": "🇨🇭",
"asn": "AS56803",
"currency": {
"code": "CHF",
"name": "Swiss Franc",
"symbol": "CHF"<
},
"time_zone": {
"name": "Europe/Zurich",
"offset": 1,
"offset_with_dst": 1,
"current_time": "2024-11-24 10:13:10.928+0100",
"current_time_unix": 1732439590.928,
"is_dst": false,
"dst_savings": 0,
"dst_exists": true,
"dst_start": {
"utc_time": "2024-03-31 TIME 01",
"duration": "+1H",
"gap": true,
"dateTimeAfter": "2024-03-31 TIME 03",
"dateTimeBefore": "2024-03-31 TIME 02",
"overlap": false<
},
"dst_end": {
"utc_time": "2024-10-27 TIME 01",
"duration": "-1H",
"gap": false,
"dateTimeAfter": "2024-10-27 TIME 02",
"dateTimeBefore": "2024-10-27 TIME 03",
"overlap": true<
}
"security": {
"threat_score": 75,
"is_tor": false,
"is_proxy": true,
"proxy_type": "VPN",
"is_anonymous": true,
"is_known_attacker": true,
"is_spam": false,
"is_bot": false,
"is_cloud_provider": false
},
"user_agent": {
"userAgentString": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.1 Safari/605.1.15",
"name": "Safari",
"type": "Browser",
"version": "18.1",
"versionMajor": "18",
"build": "Unknown",
"device": {
"name": "Apple Macintosh",
"type": "Desktop",
"brand": "Apple",
"cpu": "Intel"
},
"engine": {
"name": "AppleWebKit",
"type": "Browser",
"version": "605.1.15",
"versionMajor": "605",
"build": "Unknown"
},
"operatingSystem": {
"name": "Mac OS",
"type": "Desktop",
"version": ">=10.15.7",
"versionMajor": ">=10.15",
"build": "??"
}
IP Data
The information you reveal with this IP address allows internet players to know a lot about you without telling you:
- Geographical location (see tools section).
- Whether or not to use a VPN.
- Recording of your website visits (also using cookies).
- Saving your email address (in unencrypted email headers).
- Device and operating system type, browser, versions.
The use made of it can be:
- Virtuous:
Automatically redirect a user to the version of a site that matches their language.
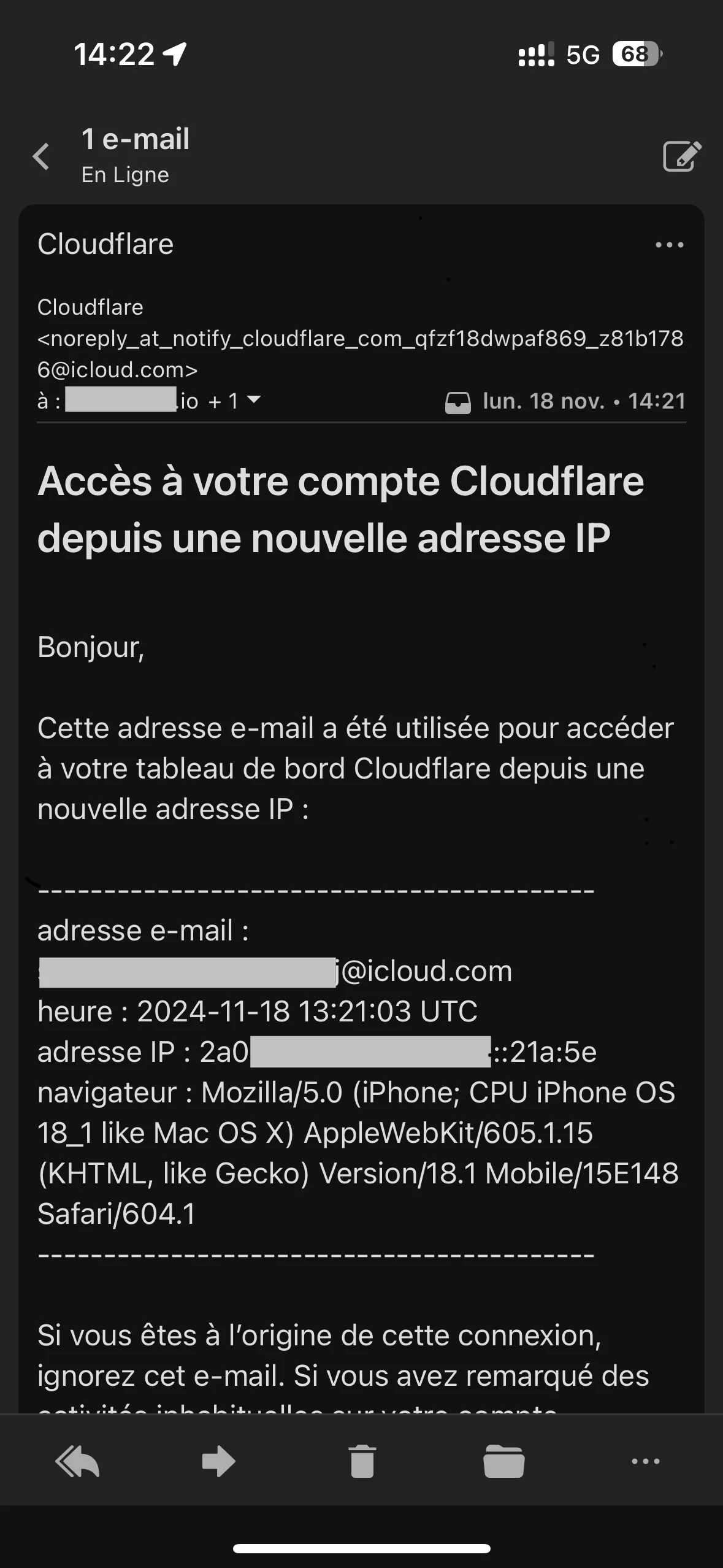
Inform a user that a connection to a site with their credentials is made from an unknown IP (fraud prevention as illustrated below). - Interested:
To track your browsing habits to build a profile of you in order to push you targeted advertisements.
Prevent you from connecting to a platform based on your location (streaming platforms).